This tutorial will cover the most used SS commands in Linux with examples to make using the SS command easier.
Knowing what connections and sockets exist within your server is key to keeping your server safe and secure. This command is much like the netstat command; however, this command is newer and provides more easily-readable output compared to its older counterpart.
We’ll look at some of the most used ss commands with examples to help make your use of this great tool easier. We will use an Ubuntu VPS running version 22.04, but this should work on any modern Linux distribution. Let’s get into it.
Prerequisites
- A Linux VPS or computer running a modern version of Linux
- Root access or a user account with sudo privileges
What is the SS command for?
The ss command, short for socket statistics, lets you get information about the sockets that are open on your Linux operating system. This command also allows you to view the connections that are made to each socket, allowing you to research and diagnose whether there are any unintended or malicious connections to your server or computer.
Overall, we recommend using this tool when configuring any services on your server to ensure that your sockets and ports are all set up exactly as you expect them to be. You can also use this tool to conclude whether to block certain IP addresses from access to specific ports on your system.
Using ss to view established connections
You can simply run the ss command without any arguments to view all open non-listening sockets that have a connection established. This is different from a listening socket, where a process is waiting for a client to connect to the service.
ss
You can see all of the sockets that have a connection established, just like this example:
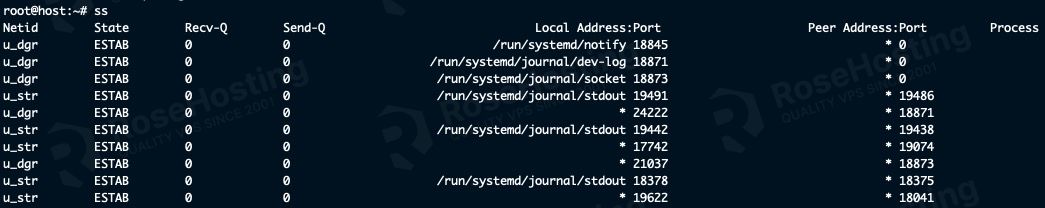
These results can be filtered by using arguments, such as a filter to view only IPv4 connections:
ss -4
You can see the results here:

This same filter can be applied to IPv6 connections by supplying the -6 argument:
ss -6
The output will look the same as the -4 command, only involving IPv6 connections.
Using ss to view all sockets
You only need to add the -a argument to get as much output as possible, revealing every possible socket status on your server.
ss -a
Here’s how that looks on our server:
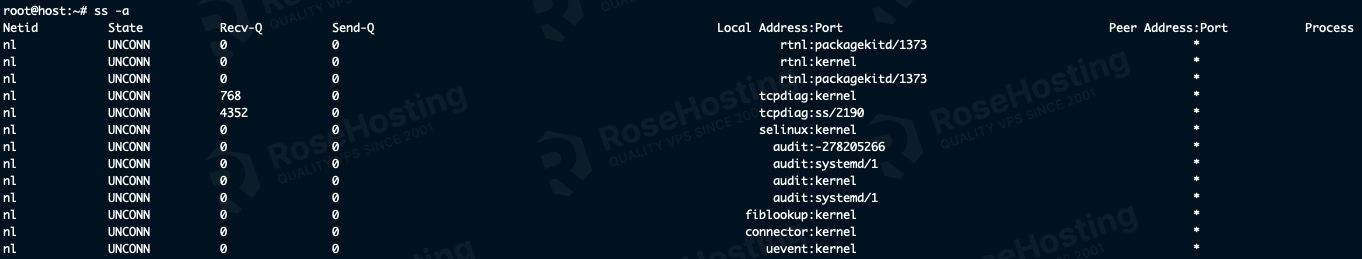
If we were to scroll down this list, we could see the various connection states. Here’s a quick rundown of what they mean:
UNCONN – Specific to UDP, UDP connections do not have any states apart from not connected or establishedLISTEN – socket is listeningESTAB – connection to the socket is establishedFIN-WAIT-1 – The remote client is requesting to close the connection with the serverCLOSE-WAIT – Server acknowledges the request to close the connectionFIN-WAIT-2 – The server lets the remote client know that the connection will be closedLAST-ACK – Server sends the close connection request to the remote clientCLOSING – The server waits for an acknowledgment from the remote client that the connection is closedTIME-WAIT – TCP specific, this keeps the socket open after the client closes the connection for a short period of time just in case.
Since the output list can get quite long, we recommend piping this command into the less command, allowing you to scroll up and down the list.
ss -a | less
Just press the Q key on your keyboard to exit this view.
Using ss to see all listening sockets
You can view your services and which sockets are open with this simple command:
ss -l
When you run this, you’ll see the sockets that are listening for connections:
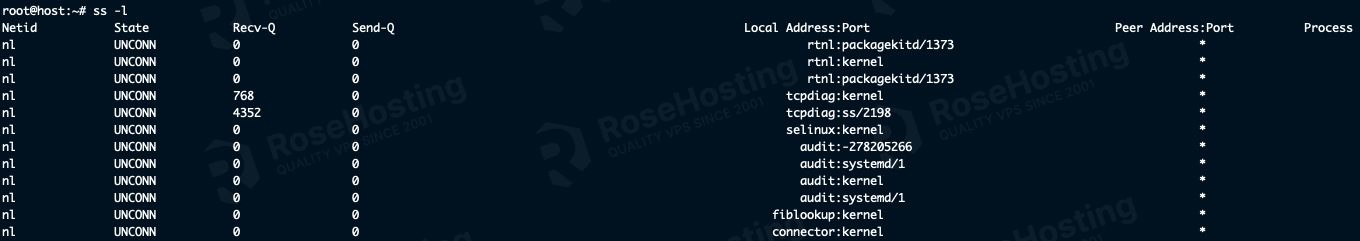
This includes sockets like Netlink, UNIX datagram, raw and datagram packet sockets, and TCP and UDP sockets.
Using ss to see all TCP socket connections
Viewing all of our TCP socket connections is very straightforward, only requiring a single option to be specified:
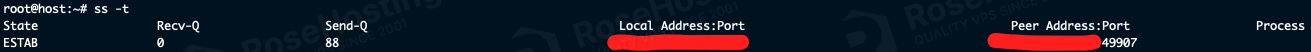
ss -t
You can then see all of your TCP socket connections and details about them:
You can also combine the arguments mentioned. For example, to see all of our sockets that are both listening and TCP, we simply combine the two options:
ss -lt
Giving you an output like this:

Viewing process information about a socket
We recommend using the -p option with any ss command you run, as it will show you the process that owns the socket. NOTE: You will need to run this as root or as a user with sudo privileges. Otherwise, it will not return the process information.
As an example, we will combine it with the previous command, which showed us our listening TCP sockets:
ss -ltp
Running this command gives us an output like this:

As you can see, our SSH daemon and our Apache2 web server are both listening with a TCP socket.
Filtering results from ss
The ss command supports some basic filtering, such as showing results with a specific source or destination IP, specific port number, or connection state, to name a few.
You can see results involving a certain destination address like so (the important part is after the -a option):
ss -a dst <IP address>
That command will give you output like this:

You can also specify a source address, like so:
ss -a src <IP address>
This is useful if your server has more than one IP address, for example.
Another example is filtering by state, such as viewing all sockets with an established connection.
ss -a state established
When you run this, you’ll be able to see all of the established connections on your server. Note that this can also include internal connections between services on your system.
Viewing ss summary information
If you want a quick and short output that gives an overview of the sockets on your server and some basic information, you can use this command to see a quick summary.
ss -s
The summary will look something like this:
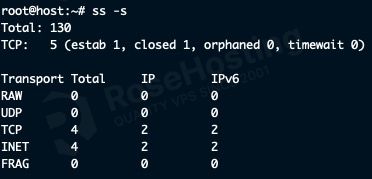
This shows you the total number of sockets, how many of which are TCP, the types of TCP connections, as well as the totals for each transport type and IP revision.
Use the manual
We highly recommend going through the manual pages to see more information about ss, as its uses are extensive. Examples include different ways of filtering information, viewing internal TCP information in-depth, checking the memory usage of sockets, or even exporting raw TCP socket information into your console or a file. You can check the man pages using the command man ss to get more information. The command ss --help is also a great, more compact way to see the basic features offered by this tool.
Did our article help you understand the connections to your server or computer? If so, please consider sharing this useful guide on social media – you never know who it might help. Do you know a better way of viewing your connections on your Linux server? Please share them in our comment section below!
